Of SMBs fail within 6 months post attack
Avg. downtime cost during a cyberattack
Avg. cost of a breach in 2023
Potential fine for data regulation non-compliance (GDPR)
Know your risks before attackers do. Many businesses assume they’re secure until they’re breached. Our free, NIST-based assessment uncovers your vulnerabilities and gives you a clear roadmap to resilience.
Your network is your first line of defense. Make it strong. Outdated firewalls and poor visibility are open invitations to cyberattacks. We secure your perimeter with modern firewalls, traffic analysis, and intrusion detection.
Still relying on antivirus? That’s not enough. Legacy antivirus tools miss ransomware and advanced threats. Our EDR solution does a whole lot more to detect attacks and roll your systems back to safety automatically.
You can’t monitor systems 24/7. But we can. AI-driven MDR detects and contains attacks in real time, often before you even know something’s wrong.
One weak password can compromise your entire system. IAM tools to ensure only the right people have access to the right data… at the right time.
90% of breaches start with a phishing attack. We train your staff to spot threats, avoid phishing, and respond smartly.
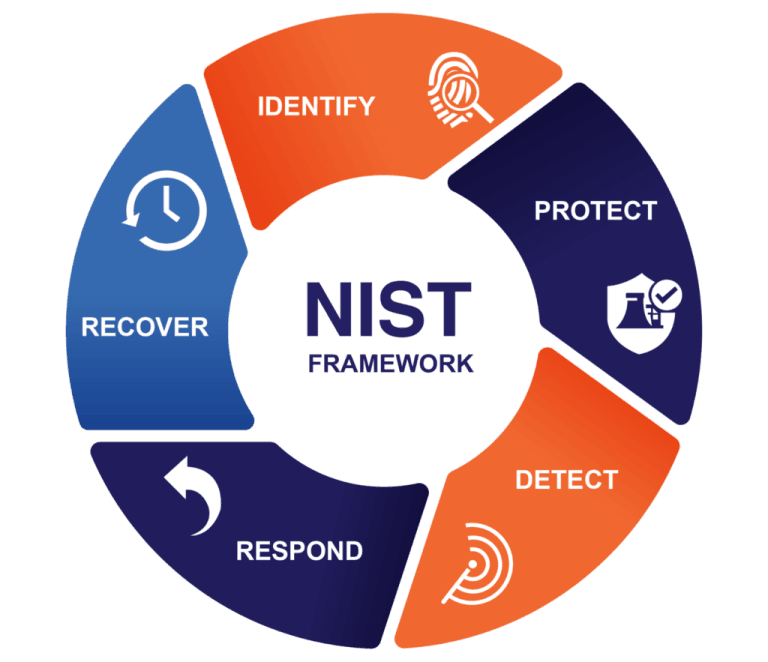
Know what you need to protect... before it’s targeted. We begin with a full assessment of your assets, systems, and risks. From asset inventory to governance mapping, we help uncover vulnerabilities and prioritize the protection of what matters most.
Put smart defenses in place before threats strike. We implement access controls, encryption, user training, and clear policies to prevent unauthorized access and reduce the risk of breaches... before they ever happen.
Spot threats early. Act faster. With 24/7 monitoring and advanced analytics, we detect suspicious activity, unauthorized access, and anomalies in real time—before they escalate into damage.
Respond with speed and confidence. Our proven incident response plans prioritize fast action, with a target of 60-second detection and 15-minute containment to minimize downtime, disruption, and cost.
Bounce back fast. Learn and strengthen. We ensure your business can recover quickly through secure backups, disaster recovery planning, and post-incident analysis—so you're not just restored, but more resilient.
We use cookies to improve your experience on our site. By using our site, you consent to cookies.
Manage your cookie preferences below:
Essential cookies enable basic functions and are necessary for the proper function of the website.
These cookies are needed for adding comments on this website.
These cookies are used for managing login functionality on this website.
Statistics cookies collect information anonymously. This information helps us understand how visitors use our website.
Google Analytics is a powerful tool that tracks and analyzes website traffic for informed marketing decisions.
Service URL: policies.google.com (opens in a new window)